Pablo de Juan Fidalgo ![]() Atos Research and Innovation, Spain
Atos Research and Innovation, Spain
Hristo Koshutanski ![]() Atos Research and Innovation, Spain
Atos Research and Innovation, Spain
According to the European Commission, critical infrastructures (CI) are all those physical or digital systems that provide essential functions and services to support the most basic social, economic, environmental, and political systems. Sectors such as health, transport or energy are examples of CI.
Regarding the energy sector, an attack can have a great impact in the society due to the dependency that we have in this sector. Some decades ago, the energy sector was characterized by its isolation from the rest of the economic components. With digitalization and the inclusion of Information and Communication Technology (ICT) in the different processes of Electrical Power and Energy Systems (EPES), together with the development of smart-cities and Industry 4.0, a new era has begun. We all agree that technology is designed to facilitate all aspects of our lives but sometimes it brings some problems with it.
Over the years we have observed that this modernization of EPES has increased the attack surface and malicious actors are continuously developing new threats against systems’ vulnerabilities[1],[2],[3].
As we have mentioned before, the energy sector is key in our society and an attack can trigger devastating consequences. Unfortunately, we have already experienced the negative impact of this kind of attacks. A great example is BlackEnergy, which targeted Ukrainian power plants in 2015 causing the disruption of electricity in half of the homes in the Ivano-Frankivsk region [4]. This kind of attacks are performed by a selected group of attackers that are enrolled in nation-sponsored groups called Advanced Persistent Threats (APT) [5]. They stand out for being stealthy and for targeting critical infrastructures that can cause high damage in their victims.
In a circular economy, everything that affects another entity will, sooner or later, affect you. That’s why it is critical to share cyber threat intelligence (CTI) information among different partners. Some of the benefits that can be listed are the obtention of refined intelligence on security incidents like feedback from other organizations, the evaluation of security measures and its effectiveness, and the mapping of threats through statistical analysis with telemetry. Refer for instance to the EU Cyber Information and Intelligence Sharing Initiative (CIISI-EU) [6] for collaborative information sharing of TI across CI sectors.
However, one of the barriers nowadays is that organizations are still reluctant to share data among other entities due to its sensitiveness, especially operators of highly sensitive infrastructures, such as EPES. They still face limitations or unwillingness to share CTI data either due to the price to use CTI platforms or due to security and privacy concerns in the open-source solutions [7], or due to the limited fine-grained control offered on what is shared and with whom.
It is important to note that any information leakage would be very risky, that’s why a carefully management of the data is unnegotiable, always in compliance with the data protection regulations, particularly the General Data Protection Regulation (GDPR) [8]. To overcome that, ELECTRON has designed a SharePoint platform (E-SP) that will be described in the following section.
The ELECTRON SharePoint Approach
The ELECTRON SharePoint (E-SP) is based on Malware Information Sharing Platform (MISP) [9] technology, offering additional features such as CTI data enrichment, finer-grained encryption and anonymization of the information published. It allows EPES end-users to communicate in a decentralized and anonymous manner. Figure 1 shows a view of the E-SP communications between different ELECTRON framework instances (per EPES operator). It allows stakeholders to share sensitive data with trusted entities by configuring privacy policies.
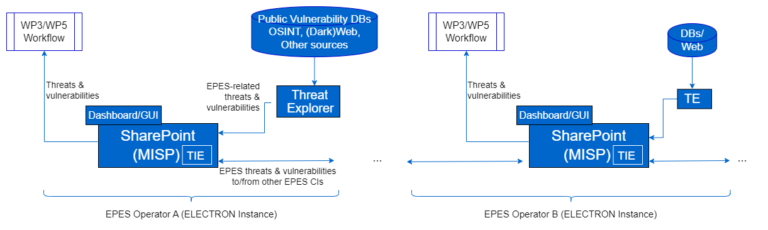
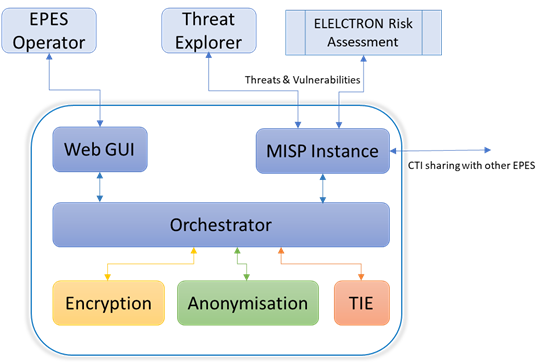
Figure 2 shows a high-level architecture view of the E-SP including the main functional components. The central component is the Orchestrator that governs the communication flow between each unit in the architecture. It works in both directions, publishing new events with protected data after calling the encryption and anonymisation modules, and receiving events from the MISP instance to perform CTI-enrichment and publishing them back. The Orchestrator has several endpoints that are accessible either via an API or through a Web GUI. The Web GUI offers a friendly interface to EPES operators to configure required CTI security and privacy settings of the E-SP, as well as interchange CTI data with other EPES stakeholders. The Orchestrator has an internal database to store any configuration and policies for its operation.
There are three main functional blocks:
- Encryption and key-management in charge of offering encryption and key management functionalities (through dedicated API) used to achieve confidential sharing of CTI between EPES stakeholders, with the possibility of fine-grained attribute-level encryption.
- Anonymisation in charge of offering data anonymisation functionality (through API) according to different privacy models of preference to an EPES operator (k-anonymity, generalisation, suppression, etc.). Anonymisation can be applied on selected attributes of CTI objects through a flexible and scalable privacy policy configuration.
- A Threat Intelligence Engine (TIE) in charge of producing a score for every event that is published in the MISP instance. This score is individual to each EPES entity as it uses the EPES operator’s infrastructure assets to calculate the risk and how relevant the event is to the assets depending on different heuristics. This process is done by ingesting indicators of compromise (IoCs), and it produces enriched CTI information.
The E-SP is part of the CYPER framework of the ELECTRON architecture. It integrates with the ELECTRON collaborative risk assessment providing information of relevant threats and vulnerabilities as shown in Figure 2. The E-SP will be evaluated under several ELECTRON use case scenarios. Some relevant KPIs for the E-SP are: i) Availability as a percentage of uptime (>= 95%), and ii) Improved automation of vulnerability and threat assessment (>=60%).
References:
[1] Z. Mrabet, et al. »Cyber-security in smart grid: Survey and challenges« Computers & Electrical Engineering vol.67, 2018. DOI
[2] https://www.tripwire.com/state-of-security/ics-security/us-government-warns-new-malware-attacks-ics-scada-systems/
[3] https://www.cisa.gov/uscert/ncas/alerts/aa22-103a
[4] “BlackEnergy trojan strikes again: Attacks Ukrainian electric power industry” – 2016, available at ESET
[5] Ivo Friedberg, Florian Skopik, Giuseppe Settanni, and Roman Fiedler. Combating advanced persistent threats: From network event correlation to incident detection. Computers & Security 48 (2015), 35–57.
[6] https://www.ecb.europa.eu/paym/groups/euro-cyber-board/shared/pdf/ciisi-eu_practical_example.pdf
https://www.ecb.europa.eu/press/pr/date/2020/html/ecb.pr200227_1~062992656b.en.html
[7] T. Wagner, K. Mahbub, E. Palomar and A. Abdallah, “Cyber threat intelligence sharing: Survey and research directions,” Computers & Security, vol. 87, p. 101589, 2019.
[8] Vladimirova-Kryukova, A.; “The Impact of GDPR on Cybersecurity Managers,” ISACA Now, 16 November 2018, https://www.isaca.org/resources/news-and-trends/isaca-now-blog/ 2018/the-impact-of-gdpr-on-cybersecurity-managers
[9] https://www.misp-project.org/
[10] Network Code for Cybersecurity aspects of cross-border electricity flows, 14 January 2022 [Online]. Available at: https://eepublicdownloads.entsoe.eu/clean-documents/Network%20codes%20documents/NC%20CS/220114_NCCS_Legal_Text.pdf
